We knew this day was coming. On a long enough timeline, the survival rate for every algorithm drops to zero. Yes, I’m paraphrasing Tyler Durden.
It’s slightly less amazing than finding a unicorn in the woods and I don’t think many will remember where they were and what they were doing on the day they first heard about it but Google’s announcement yesterday that they had successfully produced a usable SHA1 collision is a pretty big deal.
It signifies a transitional moment; the instance of time where you moved from saying, “it’s possible” to “it has happened.” Despite being technically deprecated in 2011, SHA1 is still an omnipresent thing in our lives (even though many fail to appreciate it). And now we have tangible proof that it is well and truly broken.
If you still have stuff that uses SHA1, don’t rush into freak-out mode, though. This collision that Google produced didn’t come without a significant amount of money spent and cryptographic effort. For the time being, someone will need to be really motivated to attack you in this manner. That doesn’t mean you shouldn’t be concerned, though. Imagine the problems we’ll have when bad actors start successfully producing forged web server certificates that have hashes that match the real ones. When that happens, you’ll be a target not because of who you work for but simply because you exist as an Internet-connected entity with something to steal. The same will be true when that pre-root kitted ISO image you just downloaded has a hash that matches the real deal. When that day comes you should be in full-on freak-out mode. That day is coming faster than I probably realize so your best bet is to heed the advice of many and start pushing your way past SHA1 in all of your systems. Vendors should be on notice: SHA1 isn’t welcome here any more.
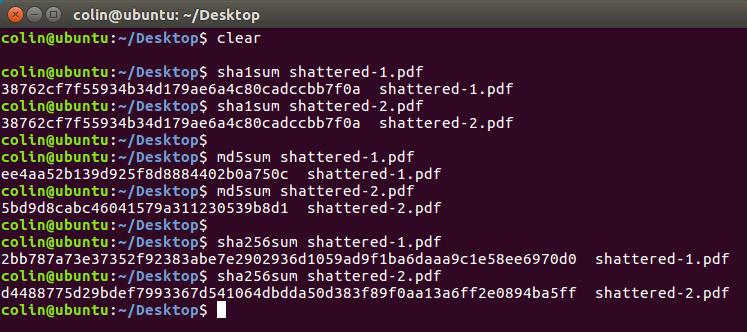
While we all digest this (see what I did there?) I do have one suggestion: when you have to use SHA1, double-check things using another hashing algorithm. Notice below that the two documents Google provided do indeed have the same SHA1 hash. They do not, however, have the same MD5 hash. MD5 is even more persona non grata that SHA1 but in this case, it’s doing you a favor by pointing out the problem.
Here are the PDF files (PDF1, PDF2):
And here are the SHA1, MD5 and SHA256 hashes of each. Trippy…
Here are the relevant links if you want to read more:
Note: Google, like many others, has been talking about this for some time: https://security.googleblog.com/2014/09/gradually-sunsetting-sha-1.html
SHA2 and SHA3!!!
Cheers,
Colin